Checkpoint Firewall Training Videos Download
Course Features
Training Type
Classroom & Online
Course Duration10 Days
No. of Hours6 Hours a Day
Certificate
Yes
Skill Level
Intermediate
PriceUSD 1000 Expressvpn download.
Study Material
Yes
Batches Available
(Mon-Fri) & (Sat-Sun)
- Overview
- Course Outline
- Batch Details
- Free Resources
- FAQs
Checkpoint Firewall Training Overview
CCSA is an abbreviation for Check Point Certified Security Administrator & CCSE is an abbreviation for Check Point Certified Security Engineering.
CheckPoint Certification Training Courses (CCSA & CCSE) Checkpoint is an industry leader in network security known as next generation and advanced firewall protection system identifies and control applications and scans content to stop threats. Checkpoint is globally accepted and widely used security solutions provider across the globe, providing security solutions to top 100 organizations.
Check Point Software Technologies provide exceptional threat prevention and security management solutions. Their latest Gen V multilevel security architecture prevents cyber attacks across networks, cloud and mobile operations.
I-Medita Checkpoint Firewall Training course proves a stepping stone for Checkpoint Certifications. You will get immediate recognition for your knowledge, experience, and abilities when you obtain the prestigious Check Point Certification.
What is the Checkpoint Firewall Training Course (CCSA + CCSE)?
I-Medita conducts Checkpoint Firewall Training course in Pune. Our Training includes class room lectures along with extensive Lab sessions. Our Check Point Firewall course curriculum is designed to cover modules of both, Check Point CCSA R80 & Check Point CCSE Certification R80.
During the Checkpoint Firewall Training Course you will gain in-depth knowledge required to configure Check Point security gateway, security policies, manage and monitor secure networks, advanced firewall, clustering and acceleration, advanced user management, advanced IPsec VPN and remote access, auditing and reporting.
Who should enroll for the Check Point Firewall Course?
- Check Point Professionals who want to improve their competencies can take this course
- Professionals who aspire to obtain CCSA / CCSE Certification should enroll for this course. This course provides you a very systematic & methodical preparation for Certification exam
Are there any prerequisites for Check Point Firewall Course?
The pre-requisite for Check Point Firewall training course is that you must have basic knowledge of TCP / IP and Windows, Unix, Networking and Internet.
Job profiles can you apply for the Check Point Firewall Course?
After successful completion of the Check Point Firewall Training course, you are qualified to apply for positions like-
- Firewall Administrator
- Network Security Engineer
- Firewall Engineer
- Network Security Administrator.
I-Medita Free Demo Session
We at I-Medita provide a Free Demo Session for security professionals interested in joining our Check Point Firewall Training Course. This way, you get an idea of how our classroom lectures are delivered. You get a tour of our ultra-modern Labs having Check Point products. You get to interact with our Certified trainers and get a picture of the scope & growth prospects in Check Point domain.
Batch Details
I-Medita conducts several batches daily for Check Point Firewall Training course in Pune. We restrict our batch size to 20 students to ensure that you get individual attention. We take great pride in the fact that all our trainers are Industry Experts and Certified Networking Professionals.
Global Knowledge
| CHECK POINT FIREWALL TRAINING (CCSA+CCSE R80) | ||
|---|---|---|
| Track | Regular (Mon-Fri) | Weekend (Sat-Sun) |
| Duration | 10 Days | 10 Days |
| Hours | 6 Hours a Day | 6 Hours a Day |
| Fees | USD 1000 | USD 1000 |
Devices to be used during Check Point (CCSA) Training
During the Check Point Firewall Training Course, we insist that you get maximum possible Practice of working with Check Point Security Gateway Appliances and Management Platforms. Our Labs are equipped with the following Checkpoint equipment’s.
- Security Gateway Appliances (Firewall): 3100/ 3200/ 5100/ 5200/ 5400/ 5600/ 5800/ 5900
- SMART-1: Security Management Platform: 405 /410 / 525 /5050 /5150
- Software Operating: R80
What will you learn in this Check Point Firewall Training Course?
Check Point Firewall Training Course concentrates on following aspects of Network Security. The objective of this course is to make you skilled at handling Check Point Security products. During the course, you will learn:
- Introduction to Check Point technology
- Deployment platforms
- Introduction to the Security Policy
- Monitoring traffic and connections
- Network Address Translation
- Using SmartUpdate
- User management and authentication
- Identity Awareness
- Introduction to Check Point VPNs
- Upgrading Check Point Modules
- Advanced Firewall
- Clustering and Acceleration
- Advanced User Management
- Advanced IPSec VPN and Check Point Capsule
- Threat Prevention
- Intrusion Prevention
- Auditing and Reporting
At I-Medita, we give emphasis to Practical Trainings and Lab Sessions. Our Training rooms have digital writing pads, AC, Wi-Fi and Projectors. Our Labs are equipped with latest Checkpoint equipments. You have 24*7 Labs access for extra practice sessions as per your convenience.
Outcomes of Check Point Firewall Training Course?
You will have thorough knowledge and understanding of technical concepts & functionalities of Check Point security Products.
- You will be competent to install, deploy, configure and manage Check Point Next Generation Firewalls.
- You will be prepared for Check Point CCSA & CCSE Certification examination
- You will be qualified to take up jobroles such as Firewall Administrator, Network Security Engineer, Firewall Engineer, Network Security Administrator.
What is the Check Point FirewallTraining Course Curriculum?
I-Medita Check Point Firewall Training Course curriculum is exquisitely designed to cover modules of both, Check Point CCSA & CCSE Certifications. This is really helpful for systematic preparation of Check Point CCSA & CCSE Certification exams.
Course Topics
- Check Point Security Management Architecture (SMART)
- The Check Point Firewall features
- Security Gateway Inspection Architecture
- Check Point Firewall Infrastructure
- Checkpoint Deployment Considerations
- Check Point Smart Console Clients
- Security Management Server
- Securing Channels of Communication
- Check Point Deployment Platforms
- Check Point Gaia
- Security Policy Basics
- Managing Objects & Creating the Rule Base
- Rule Base Management
- Policy Management and Revision Control
- Policy creation
- SmartView Tracker ,SmartView Monitor
- Monitoring Suspicious
- Activity Rules
- Gateway Status
- SmartView Tracker vs.SmartView Monitor
- Introduction to NAT & Manual NAT
- SmartUpdate and Managing Licenses
- Viewing License Properties
- Service Contracts
- Creating Users and Groups
- Security Gateway Authentication
- User Authentication, Session Authentication & Client Authentication
- LDAP User Management with
- UserDirectory
- Introduction to Identity
- The Check Point VPN
- VPN Deployments & Implementation
- VPN Topologies
- Special VPN Gateway Conditions
- Access Control and VPN Communities
- Integrating VPNs into a Rule Base
- Remote Access VPNs
- Corporate and Branch Office
- Backup and Restore Security Gateways and Management Servers
- Upgrading Standalone Full High Availability
- VRRP, Clustering and Acceleration
- ClusterXL: Load Sharing
- Maintenance Tasks and Tools
- Management HA
- SecureXL: Security Acceleration
- CoreXL: Multicore Acceleration
- Advanced VPN Concepts and Practices
- Remote Access VPNs
- Multiple Entry Point VPNs
- Tunnel Management
- VPN Debug
- Third Party Certificates
- Security VPN
- SmartEvent, SmartEvent Architecture &SmartReporter
For more in-depth course curriculum information – please check Check Point Firewall Training Course Curriculum Details .
Training Labs
We have state of the art Training Labs and provide extensive Lab sessions for Practical implementation of Check Point products. With such detailed practice, you will become confident to configure and manage Check Point Next Gen Firewalls. Our Lab sessions comprise of following :
- Explore Checkpoint Firewall Features
- Distributed Installation
- Branch Office Security Gateway Installation
- CLI Tools
- Building a Security
- Configure the DMZ
- Monitoring with SmartView Tracker
- Configure NAT
- Configuring User Directory
- Identity Awareness
- Site-to-site VPN Between
- Core CLI Elements of Firewall Administration
- Migrating to a Clustering Solution
- Configure Site-to-Site VPNs with
- Remote Access with Endpoint
- Configuring SmartDashboard to Interface with Active Directory
- Configure Site-to-Site VPNs with Third Party Certificates
- Remote Access with Endpoint Security VPN
- SmartEvent and SmartReporter
Post Training Support & Placement
When you register for I-Medita Check Point Firewall Training Course, we provide you the option to attend 3 refresher trainings, at no extra fees. We solve your questions, doubts 24*7 via Chat, Whatsapp and Emails
We give 100% placement support to our students. We guide you for impressive resume preparation, approaching Job interviews confidently & more. We have put together a question bank with 100+ network security questions based on theory and practical sessions. This study material is very helpful for the methodical preparation of Interviews & certification exams.
Checkpoint CCSA & CCSE Certification- Exam Preparation
Following are the 2 most popular Check Point Certification Exams
| Exam Code | Exam Name |
|---|---|
| #156-215.80 | CCSA – Check Point Security Administration R80 |
| #156-315.80 | CCSE – Check Point Security Engineering R80 |
Upcoming Trainings
| DATE | COURSE | TRAINING TYPE | BATCH | CITY | REGISTER |
|---|---|---|---|---|---|
| 23 Sep 2019 | Check Point | Classroom / Online | Regular Batch (Mon-Fri) | Pune | ENROLL NOW |
Can't find desired training? Request for a training
free Resources
VPN Interview Questions Guide
Frequently Asked Questions
Check Point CCSA& CCSE Certification Exam - Prerequisites
- CCSA Certification pre-requisites: Knowledge of TCP/IP and routing fundamentals.
- CCSE Certification pre-requisites: You should have cleared CCSA Certification
Check Point CCSA & CCSE Certification Exam - Scheduling an Exam
Please schedule your CCSA & CCSE examination via the Pearson Vue Website https://home.pearsonvue.com/checkpoint/op
Pearson Vue are authorized testing vendors for Check Point Professional Certification
Check Point CCSA & CCSE Certification Exam - Question Formats
Check Point CCSA & CCSE Certification Exam comprises of the following questions.
- Multiple choice questions
- Scenarios based questions
Questions will not have multiple answers. You will have to “Select the Best” answer
CCSA & CCSE Certification Exam - Duration, No. of Questions, Passing Score
Duration of Check Point CCSA & CCSE Certification exam is 90minutes. You have to answer 100 questions in 90 minutes. You are required to score more than 70% marks to achieve the certification.
Check Point CCSA & CCSE Certification Exam - Cost / Fees
Check Point CCSA & CCSE Certification fees are $250 + Local Taxes. Fees are payable in US Dollars.
Check Point CCSA & CCSE Certification – Validity
Check Point CCSA& CCSE Certification are good / valid for Two years. Please ensure that you renew your certification before it expires.
Saurabh Yadav
Triple CCIE R&S, SP, Security # 46962
Baldev Singh
CCIE Security # 37094
Juniper Firewall Training
Sudhanshu Bhat
CCIE Voice # 41212
Surendra Singh
CCIE R&S # 60346

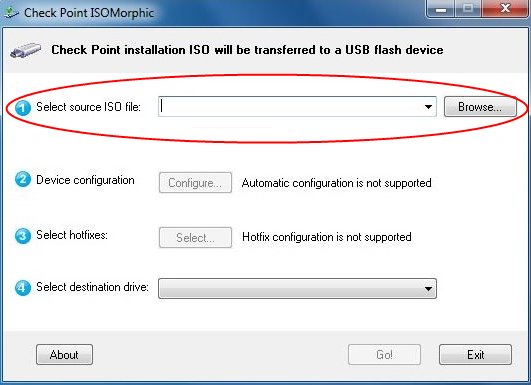
Checkpoint Firewall Training Videos Download Free
Interview Guides
Self Study Guides
Useful Blogs
Important Links
Services
© 2019, I-Medita Learning Solutions. All rights reserved.
Security Management Architecture (SMART)
Checkpoint deployment have basically two types of Security Management Architecture(called SMART)
Distributed
Standalone
SMART Components
Console (SMART Console PC)
Security Management Servers
Firewall Gateway
In this above scenario, the SMART is consisting of 3 components.
Smart Console – A host computer is the SMART topology taht runs the smart console software modules(smart dashboard, smart tracker, smart monitor and so on). It create the policies and store it into the management server.
Security Management Server –All the policies of the SMART network stored in management server/smart security server. The management server push the policies over the Firewall Gateways. In a SMART topology there could be a several numbers of gateways, but a single management server itself is enough to manage them, can be able to manage all tghe FW-GW in a centralized manner.
Security Gateway – The checkpoint appliance that implement the policies and enforce policies and access control mechanism over packet traversing rules.
Deployment Methods
Now that you know what is what, the architecture of Check Point firewalls should be a little easier to understand. Check Point firewalls can be deployed in a standalone fashion or a distributed one. Lets look at the difference between the two
Standalone Deployment
In a stand-alone deployment, your Security Management Server and Security Gateway is installed on the same platform and your smart console will most probably be installed on a separate platform with which you will access the Security Management server to create policies and push it to the Security Gateway (which is the same device in this case). However, this deployment defeats the whole purpose of Check Point’s three-tiered architecture and is not recommended by Check Point, except for small businesses.
Distributed Deployment
A distributed deployment is more commonly known as a Three-Tired architecture, wherein each component is installed on a separate platform and this type of deployment is highly recommended by Check Point. Smart Console is usually installed on Windows for its ease of use. Security Management Server can be installed on Windows/Linux/FreeBSD platform depending on the requirement. And the Security Gateway too can be installed on a Windows/Linux/FreeBSD platform as per the requirements.
The command chain between SMART components
Noet: The SMART console never interact with FW-GW directly. The SMART will always follow the command chain whenever any management action require.
Active Model (Hybride)
The Checkpoint(Almost all security appliances in this era) works in Hybrid Model
(a strip-down version of OSI Reference Model and TCP-IP Suite) .
Traffic Control Mechanisms
1. Packet Filtering :
In packet filtering the the policies are explicitly defined that what packet should be accepted and what should be dropped. These policies are based on Transport and Network Layer and decisions are taken using IP and Port addresses.
Packet filtering lets you control (allow or disallow) data transfer based on:
The address the data is (supposedly) coming from
The address the data is going to
The session and application protocols being used to transfer the data
Vulnerabilities: Using packet filtering we can filter and manage outside traffic. But a user from the inside network trying to access a non legitimate outside resource cant be managed as the response come from outside.
2. Stateful Filtering :
In stateful filtering the FW inspects the packets and remember the port numbers during a session(TCP/UDP). These inbound and outbound port numbers of a TCP/UDP sessions are stored in a lookup table(called state table) . The firewall is having an inspect engine that make it possible to filter any non legitimate traffic during a TCP/UDP session.
Bellow here two example of stateful filtering based on TCP and UDP sessions respectively.
Vulnerabilities: Stateful filtering also raise the possibility that individual hosts can be tricked into soliciting outside connections.
Suppose a user BOB wants to telnet a resource. However he can use a proxy server to encapsulate Telnet(Port-23) traffic over HTTP(Port-80) as a payload of HTTP and overcome the policy obstacles.
The stateful packet filter firewall provides no protection whatsoever from an application layer attack. In order to be effective and address today’s application layer attacks, firewalls must inspect the application layer traffic. This is the reason why today many stateful packet filter firewall vendors are adopting some form of application layer filtering. Also, recent statistics show that stateful packet filter firewalls are prone to denial-of-service attacks.
3. Application Awareness:
It is a type of traffic control method actually take a look into the Application Layer. It inspects the content of the data.
Checkponit scope
Detects and controls application usage
- Identify, allow, block or limit usage of applications, and features within them
- Enable safe Internet use while protecting against threats and malware
- Leverage the world’s largest application library with more than 6,600 web 2.0 applications
Supports advanced identity awareness for stress-free policy enforcement
- Create granular policy definitions per user and group
- Integrate seamlessly with Active Directory
- Protect environments with social media and Internet applications
Provides proven gateway security in a single, dedicated appliance
- Rely on 24/7 advanced protection
- Reap the benefits of application control and intrusion protection (IPS), as well as extensibility support for additional security capabilities
- Get greater understanding into security events with integrated, easy-to-use centralized management
- Join more than 170,000 customers, including 100 percent of Fortune 100 companies
Identity awareness
Great security involves limiting and tracking access to sensitive data and resources. With the Next Generation Firewall, your administrators get detailed visibility into the users, groups, applications, machines and connection types on your network so they can assign permissions to the right users and devices. The firewall makes it easy and cost-effective to enforce security policy, giving granular permission control over these entities; this results in superior protection across the entire security gateway.
Seamless and agent-less integration with Active Directory provides complete user identification, enabling simple, application-based policy definition per user or group directly from the firewall. Users’ identification may be acquired in one of three simple methods:
- Querying the Active Directory
- Through a captive portal
- Installing a one-time, thin client-side agent
Application controlEmployees are using more apps than ever, and you’re on the hook to protect them regardless of what they use. Check Point Next Generation Firewall has the industry’s largest application coverage, with more than 6,600 applications and 260,000 social network widgets included. You can create granular security policies based on users or groups to identify, block or limit usage of web applications and widgets like instant messaging, social networking, video streaming, VoIP, games and more.
Logging and statusTo help you make sense out of your security event data, we included SmartLog, an advanced log analyzer that delivers split-second search results providing real-time visibility into billions of log records over multiple time periods and domains
Integrated security management
Our unified security management simplifies the monumental task of managing your security environment. You’ll see and control threats, devices and users with a highly intuitive graphical interface providing views, details and reports on your security health. Manage all your Check Point gateways and software blades from one comprehensive, centralized security dashboard.
Intrusion prevention
Next Generation Firewall includes the Check Point IPS Software Blade, which secures your network by inspecting packets traversing through the gateway. It is a full-featured IPS, providing geo-protections and frequent, automated threat definition updates. Because the IPS is part of the integrated Software Blade Architecture, you’ll get all the deployment and management advantages of a unified and extensible solution.
Problem with App Awareness
Every-time the FW needs to dig into the content of the Application Layer that will further impact on the response of the hardware appliance.
Actually not everytime , but a one time inspection of Application Layer data facilitates the App Awareness. The FW checks the legitimacy of the content for the first time when the connection(TCP/UDP) going to establish. Then firewall remember the session and give the control to the L2.5 Kernel. From here the rest of the packet forwarding(inward/outward) responsibility goes to the Kernel itself and the Kernel continue to do so until the session terminates.
Underlying Platforms to Implement the Checkpoint Security Management Software
IPSO
Secure Platform(SPLAT)
GAiA
Network Diagram

Before move on to the Installation part, take a look into the SMART network diagram.
We will provision a portion of this topology in the following discussion.